Has your money ever been debited, but you did not authorize it? That’s a scary thought. Isn’t it?
Over a period of time, these strange transactions grew more and more. Banks needed to find out what was happening, and sometimes even track why strange transactions were taking place with certain accounts. This is how anomaly detection started being utilized in banks.
Data mining’s anomaly detection process, also known as outlier analysis, seeks out data points, occasions, and/or observations that differ from a dataset’s typical pattern of activity. Unusual data can point to serious occurrences, like a technological malfunction, or to promising opportunities, like a shift in consumer behavior.
Why Do You Need Anomaly Detection?
For more than 20 years, anomaly detection and rules-based techniques have been used to address fraud, corruption, and abuse. Despite being effective instruments, they still have their limitations.
Nowadays, almost every data log activity generates digital fingerprints. Companies have a big chance to stop future damage because of this. However, it frequently isn’t taken into account until after the harm has already been done.
Nowadays, a wide range of industrial industries are quite interested in anomaly detection. The technique seeks to locate data regions with unexpected behaviors or patterns using a variety of machine learning methods. Leaders across a wide range of industries can benefit from these new tools and technologies to identify possible issues early on and prevent harm.
Finding anomalies can prevent a little problem from growing into a time-consuming, widespread issue. Companies may analyze patterns, spot opportunities and dangers, and gain a competitive edge using anomaly detection by utilizing the most recent machine learning techniques.
Types of Anomaly in Datasets
The general integrity of the data recorded in the database will gradually deteriorate if normalization is not performed on datasets. Data abnormalities are specifically to blame for this. Data that does not match the real-world the database claims to represent is a natural result of these abnormalities. The creation of tables that will introduce anomalies into the database was significantly mitigated by the normalizing procedure.
Accurate real-time time series data analysis is essential for successful anomaly identification. A succession of values across time makes up time series data. This means that each point typically consists of two items: the timestamp for the measurement of the metric and the value of the metric at that moment.
Also Read: How is 5G Technology Benefiting Multiple Industries Across The Globe?
Prior to detecting time series anomalies, major KPIs’ typical behavior must be established as a baseline. Time series data anomaly detection systems can monitor seasonality—the cyclical patterns of behavior within important datasets—once that baseline is understood.
Anomalies in your business data typically fall into one of three categories: global, contextual, or collective.
Global
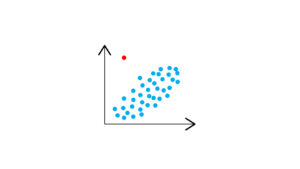 These outliers, often referred to as point anomalies, are located distant from the center of a data set. These are outliers in their most basic form. A data point is considered a global outlier in a dataset if it significantly differs from every other data point in the dataset. Most outlier identification techniques focus on locating global outliers.
These outliers, often referred to as point anomalies, are located distant from the center of a data set. These are outliers in their most basic form. A data point is considered a global outlier in a dataset if it significantly differs from every other data point in the dataset. Most outlier identification techniques focus on locating global outliers.
Collective
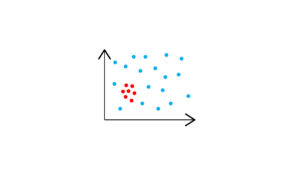 As the name suggests, a group of data points in a dataset are considered to be collective outliers if they significantly deviate from the rest of the dataset. In this situation, individual data objects might not behave as outliers, but the group as a whole might. To find these kinds of outliers, we might need to have a foundational understanding of the connections between the data objects exhibiting the outlier behavior.
As the name suggests, a group of data points in a dataset are considered to be collective outliers if they significantly deviate from the rest of the dataset. In this situation, individual data objects might not behave as outliers, but the group as a whole might. To find these kinds of outliers, we might need to have a foundational understanding of the connections between the data objects exhibiting the outlier behavior.
Contextual
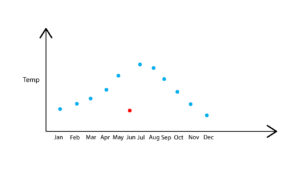 Conditional Outliers is another name for them. If a data object in a certain dataset significantly differs from the other data points due to a particular event or condition. It is possible for a data point to behave normally in one setting while being an outlier in another. Consequently, a context must be mentioned in the problem statement in order to detect contextual outliers.
Conditional Outliers is another name for them. If a data object in a certain dataset significantly differs from the other data points due to a particular event or condition. It is possible for a data point to behave normally in one setting while being an outlier in another. Consequently, a context must be mentioned in the problem statement in order to detect contextual outliers.
Users have the freedom to examine outliers in a variety of contexts with contextual outlier analysis, which can be very beneficial in many applications. The characteristics of the data point are determined using the environmental and behavioral attributes.
Anomaly Detection in Action
The main use cases for anomaly detection include anomaly-based intrusion detection, fraud detection, anomaly detection on social media platforms, anomaly detection in internet of things (IoT) big data systems, data loss prevention (DLP), anomaly detection in logs, anomaly-based malware detection, medical anomaly detection, industrial/monitoring anomalies, and anomalies in video surveillance.
Finance – Each minute, financial transactions totaling trillions of dollars take place. Real-time detection of fraudulent banking activities can give firms a competitive edge.
Manufacturing – Nowadays, sensors are incorporated in a wide variety of machinery, vehicles, and equipment. With connected Internet of Things (IoT) devices, data-driven manufacturers can keep track of all of their machinery, vehicles, and equipment in real time. To avoid expensive breakdowns and disruptions, they might use an anomaly detection solution to monitor all of their outputs.
Healthcare – In the healthcare sector, insurance fraud is widespread and costs the industry billions of dollars in payouts to fraudsters. To ensure that no payments are made to bogus accounts, insurance firms must identify false claims.
Industrial Equipment – Many top manufacturers are beginning to adopt autoencoders since manually checking for flaws and abnormalities can cost them more time and money. Employing an autoencoder approach, businesses may monitor and immediately identify any unexpected events utilizing sensor data from manufactured components.
Inferring on This..
Businesses have been focusing intensely on data collection optimization; now is the time to use that data to gain insights that can advance your business by promptly detecting and resolving problems.
As technology keeps on developing, anomaly detection is proving to be more than just a technology, – it’s a Lifesaver!