As data privacy regulations and enforcement penalties pick up pace, so do uncertainties for businesses. Many compliance regulations over the last 20+ years, including the Health Insurance Portability and Accountability Act of 1996 (HIPAA), the HITECH Act, PCI-DSS, and others, have set a historical precedent for what’s inevitably to come in data privacy compliance.
As compliance regulations evolve through the years from establishment to enforcement, businesses also follow a path of implementing the bare minimal compliance to conform to the text of the law. Most regulations also mature over time as they adapt to market realities. For example, PCI-DSS v1.0 evolved and matured over the years since its inception in 2006 to its current iteration (PCI-DSS v3.2.1) to protect cardholder data and reduce fraud. The same pattern in data privacy compliance should follow as the California Privacy Protection Agency (CPPA) begins enforcing the California Consumer Privacy Act (CCPA) more actively.
Recently, businesses got a first look into what CCPA enforcement may look like when beauty retailer Sephora was fined $1.2 million for selling consumers’ personal information (PI) without their consent. History tells us that active enforcement and penalties, like we have seen with the General Data Protection Regulation (GDPR), HIPAA/HITECH, PCI-DSS and other compliance regulations over the years, are likely to accelerate businesses’ commitment to comply with data privacy compliance. But it will take time.
According to research conducted by CYTRIO during Q2 2022, 91% of companies are not prepared for CCPA privacy compliance as enforcement begins to take effect. Most companies are still at the starting gate of where to begin with data privacy, doing nothing or having the bare minimum in place.
Also Read: How is Anomaly Detection A Shield of Security for Multiple Industries?
While many companies are just starting in their data privacy journey, it’s likely that most will follow a 3-stage maturity curve (figure 1) we’ve seen with other compliance regulations that have come before. Here are the stages that companies are most likely to navigate through in their data privacy compliance journey:
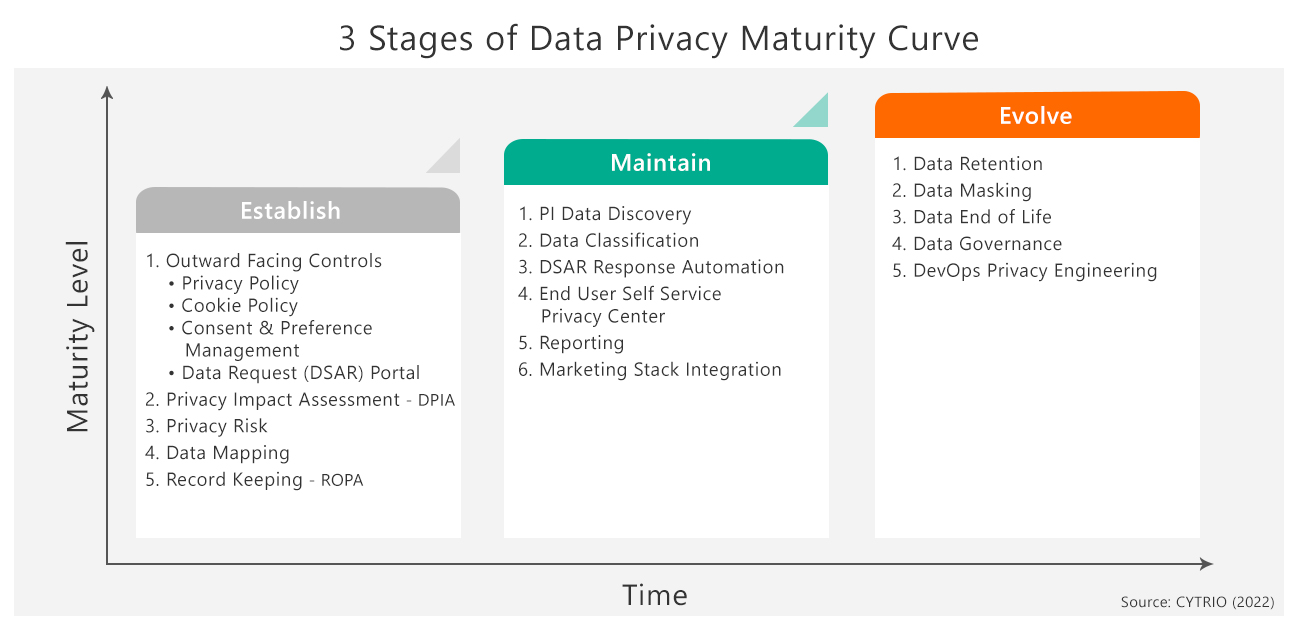
1. Established Stage
Most companies have been collecting personal information from consumers and employees for years and need to start with understanding what this data is. What personal information does the company have? For what purpose is the information being collected? Where is it located? How is the information being shared? Conduct a Data Privacy Impact Assessment to identify risks arising out of the processing of personal information and to minimize these risks. Create a risk map of where the risk exposure is in collecting, storing, using, sharing, and processing personal information.
Often managed by marketing teams, four outward facing components of outward facing controls need to be put in place during this stage: Notice and Policy, Consent Preference Management, Cookie Policy and Management, and Data Subject Access Request (DSAR) Portal for end users to easily submit data requests. Companies need to develop a well-defined Privacy Notice and Privacy Policy that clearly articulates and informs both internal and external stakeholders on what the company’s position is as it relates to CCPA and other applicable data privacy regulations.
DSAR Portal provides a mechanism for consumers to exercise their data privacy rights. Consent and Preference Management makes sure you are receiving consent from the consumer at the time you’re collecting their personal data. As part of Cookie Policy and Management, the company needs to disclose what information they are collecting and what cookies are used by the company.
You also need the ability to understand data mapping, and where and how data is mapped. In this phase, businesses are moving away from using Excel spreadsheets and other manual processes to a more efficient, effective automated solution. Understanding the impact that data privacy has on your business becomes less manual and time intensive with automation. Businesses are also continuously ensuring stored data meets the requirements of various applicable data privacy regulations.
In CYTRIO’s research, nearly 45% of companies are in the Established Stage which is relatively easy for most companies to achieve. Most companies will start their data privacy compliance journey with the Established Stage and may take 6-12 months to move to the Maintain Stage.
2. Maintain Stage
Once processes are in place for understanding what data is being collected, how it is stored, used, processed and shared, risk exposure is understood and notices and consents are in place, the next step is maintaining what has been established. How do you make sure you are maintaining what has been put in place?
Companies need a mechanism to continuously analyze, measure, and report on how your privacy program is working and responding to end user data requests while continually reducing data privacy risk exposure. Companies must think about connecting front end privacy controls with their marketing stack to make sure they are honoring end user consent and preferences. Implement a self-service portal to allow end users to manage their preferences.
As DSARs pick up in volume and frequency, companies must look to implement DSAR response automation solutions that can validate, request or identify, automatically discover all PI data, provide response workflows, and share data securely in response to a data request. These automation tools will reduce the cost of DSAR response from approximately $1,400/request to less than $200-300 per request.
3. Evolved Stage
This stage helps put mechanisms in place to proactively develop and incorporate data privacy principles in all aspects of your company. If you’re building applications that are collecting personal information, DevOps Privacy Engineering (shift-left privacy) builds controls upfront to comply with data collection and consent mechanisms, making sure that ultimately, as the application collects data, it will be used for the right purposes. The Evolved Stage includes data governance, data masking, and data retention to make sure the right people and processes are accessing PI data for the right purpose, and data is not being mis-used and deleted beyond stated purpose.
In the data privacy compliance journey, the Evolved Stage is likely years away. Businesses cannot successfully implement the Evolved Stage or even the Maintain Stage without successfully and comprehensively implementing the Established Stage first. Don’t know where to start? Start with a well thought out privacy program which includes understanding your privacy risk exposure, what PI data you have, where it is, and how it is being stored, processed, shared, and used.
As California Privacy Rights Act (CPRA) goes into effect on January 1, 2023 with expanded rights for consumers and employees, we’ll not only see companies establishing privacy policies, we’ll start to see companies move along the maturity curve. Ultimately, that will result in better privacy and protection for consumers.