Integrating security practices early in the software development lifecycle is essential, especially in light of recent events like Twilio’s Authy App security breach, which exposed millions of phone numbers. This underscores the critical need for robust security measures to safeguard applications from cyber threats. This brings us to our topic: the DevSecOps pipeline.
DevSecOps is short for development, security, and operations, which is a methodology that incorporates security procedures at every stage of the software development process. From the statistic above, we know that it’s important. Now let’s understand how you can build one, its benefits, challenges, and more.
What is a DevSecOps Pipeline?
 DevSecOps pipeline is a CI\CD pipeline that includes integrated security practices by following specific practices and functions like policy enforcement, static analysis, threat intelligence, scanning, etc. It guarantees that application security is included in the development process right from the source code.
DevSecOps pipeline is a CI\CD pipeline that includes integrated security practices by following specific practices and functions like policy enforcement, static analysis, threat intelligence, scanning, etc. It guarantees that application security is included in the development process right from the source code.
Agile practices+ Architecture + Process+ Culture =DevSecOps Pipeline
Simply put, the DevSecOps pipeline is a process where you start planning for security from the beginning itself. This ensures that each step doesn’t have any security vulnerabilities. This way, you protect it as you build, rather than trying to fix security problems later.
Note: CI/CD pipelines are processes that use automated tools and feedback mechanisms to move developer source code through many phases, including building, functional testing, security scanning, packaging, and deployment.
Also Read: GitOps: What It Is? Benefits, Challenges, Principle
Why Is DevSecOps Pipeline A Game-Changer For Your Business?
 The importance of the DevSecOps pipeline is paramount. Studies reveal that about 60% of engineers now release code twice as quickly thanks to DevOps (Development and Operations) principles.
The importance of the DevSecOps pipeline is paramount. Studies reveal that about 60% of engineers now release code twice as quickly thanks to DevOps (Development and Operations) principles.
Companies become more collaborative and efficient when they embrace a security focus from the start of a project, often known as shifting left. A lack of communication between cybersecurity and development teams typically results in project bottlenecks and costly reworks. With cybercrimes anticipated to cost $10.5 trillion annually by 2025, this is a costly mistake for your business.
It also results in developers performing only what is necessary to get software approved for deployment. By turning this paradigm upside down and fostering a culture where security is ingrained in everything, shifting lift eventually boosts throughput and quality.
What are the 3 Pillars of DevSecOps?
- Culture: DevSecOps necessitates a change in mindset where development, security, and operations teams view security as a shared duty. It encourages teamwork, dialogue, and an attitude of constant security practice improvement.
- Automation: By facilitating uniform and effective security procedures throughout the software development lifecycle, automation is essential to DevSecOps. Find and fix problems early in the pipeline, it entails automated security testing, vulnerability scanning, compliance checks, and other security-related operations.
- Integration: A key component of DevSecOps is the direct integration of security procedures into the DevOps workflow. Every phase of the process, from design and coding to testing and deployment, incorporates security safeguards. Organizations may make sure that security is an integral element of development rather than an afterthought by incorporating security controls and technologies.
Together, these three pillars provide a comprehensive approach to software development that puts security first right from the beginning and guarantees the timely and successful delivery of secure products.
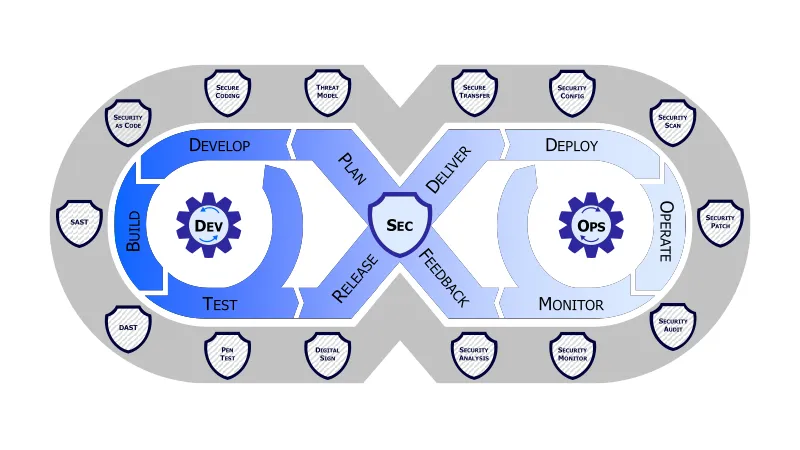
DevSecOps Pipeline Diagram Explained
The DevSecOps pipeline diagram gives a rough idea of the procedures involved in the process.
- Planning: Start by figuring out what security measures and rules you need to follow for your project.
- Code: Keep track of all the changes you make to your source code using version control systems.
- Build: Automate the building process and use tools like SAST (Static Application Security Testing) to find any security problems in your code early on.
- Test: Set up automated security tests, such as unit tests and DAST (Dynamic Application Security Testing), to catch and fix security issues before they become a problem.
- Release: Ensure your code changes are delivered smoothly and securely to the staging or production environments, with a focus on safe deployment and infrastructure setup.
- Deploy: Once your application is up and running, keep a close watch on it for any security threats or vulnerabilities and act quickly to fix them.
- Operate: Keep your application secure by continuously monitoring for any security threats and being ready to respond if something goes wrong.
- Monitor: Always keep an eye on your application and infrastructure to catch and deal with security events as they happen.
Remember, these steps can look a little different depending on the organization and the specific needs of the project.
How to Build a DevSecOps Pipeline?
Building a DevSecOps pipeline involves several essential steps tailored to organizational needs and tools used:
- Define Security Requirements: Identify specific security needs, compliance standards, and policies for implementation.
- Integrate Security into SDLC: Embed security practices across planning, coding, testing, and deployment phases.
- Automate Security Testing: Implement tools like SAST, DAST, and SCA to continuously validate security.
- Implement Security Controls: Integrate access controls, encryption, and secure coding throughout the pipeline.
- Establish Security Gates: Set checkpoints for security reviews and compliance checks before advancing stages.
- Promote Collaboration: Foster teamwork among development, security, and operations for shared responsibility.
- Monitor and Respond: Implement real-time monitoring and incident response to address security events promptly.
- Continuously Improve: Assess performance, gather feedback, and refine practices to enhance security posture over time.
What Are DevSecOps Services and Tools?
Here are some of the most essential tools and services that enterprises can use to build out their DevSecOps pipelines:
Static Application Security Testing (SAST)
SAST tools scan source code for issues, such as common vulnerabilities. These tools help developers identify and fix security problems early in the development process.
Interactive Application Security Testing (IAST)
This combines the capabilities of SAST and DAST into a single, more holistic solution. This combination allows for both code analysis and runtime scanning, offering a robust approach to application security.
Dynamic Application Security Testing (DAST)
DAST tools look for security flaws in apps while they’re running. By identifying flaws that source code scans would overlook, these technologies offer a more thorough evaluation of security.
Source Composition Analysis (SCA)
SCA tools identify libraries and dependencies within an application and enumerate the associated vulnerabilities. By understanding the components that make up an application, developers can address potential security risks more effectively.
Vulnerability Scanners
Vulnerability scanners are tools designed to detect misconfigurations and issues that can compromise security and compliance. These tools help maintain the security posture of an application by identifying weaknesses that need to be addressed.
Creating a Strong Pipeline
In my view, the true power of the DevSecOps pipeline lies in its ability to transform how teams work together, breaking down silos and promoting a shared responsibility for security. This comprehensive approach not only enhances the security posture of applications but also accelerates the delivery of high-quality software. Embracing DevSecOps is not just a necessity but a strategic advantage for businesses aiming to thrive in a digital world.